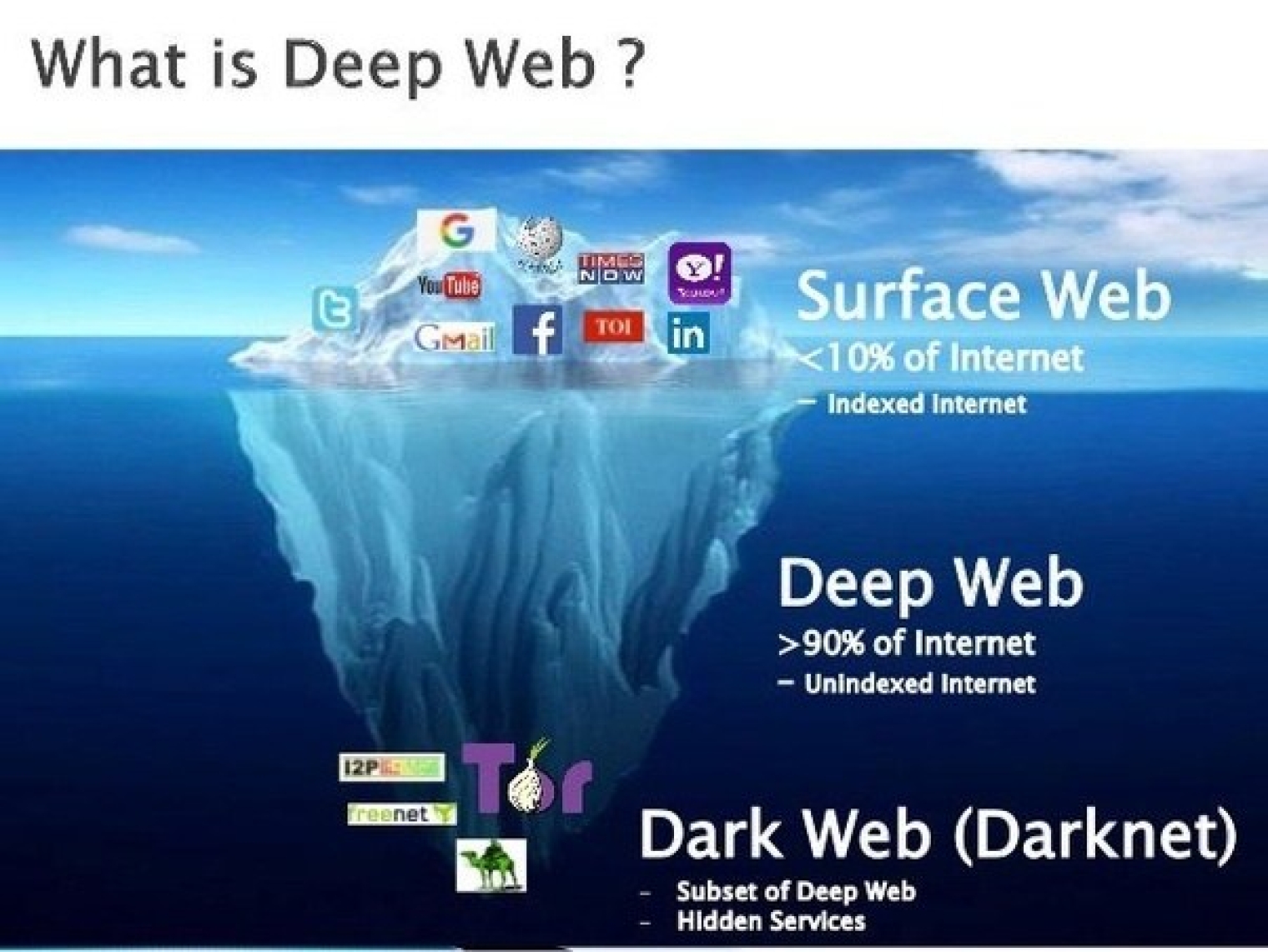
Downloading the Tor Browser is no more complicated than downloading Google Chrome. The basic code of the browser is actually based on Mozilla's. Tor dark web, clickthe 'Get NordVPN' button. All it takes is downloading darknet software. Launch the Tor browser once VPN is active and start accessing the tor dark web you are done. Tor and the Onion Browser Inside the Tor network, sites cannot use regular domain names. Instead, they use pseudo-domain names ending in. Tor is open-source software for enabling anonymous communication on the Internet. It obfuscates the source and destination of a web request by. Onion. To access the dark web, you can download and install the free Tor browser. (You can also use it to browse the surface and deep web.
Is using the Tor network illegal. Tor Browser The Onion Route. The Deep Web Sites, Dark vice city market link web, Hidden Wiki is accessed using Tor that contains, TorChan is one of the most popular deep web forums today. The dark web is an area of the internet that is only accessible with specific browser software, such as Tor or I2P. It is a web of anonymity. 12 steps. Dark Web Markets 2021 Darknet Deepweb Market Links. Not hiring hackers. Nov 02, 2021 The Safe Dark Web Links List Best for Tourists Tor Sites.
Tor Browser The Onion Route. Comprenez le Darknet Dcouvrez les diffrences entre Deepweb et Darkweb Accdez facilement au web cach grce TOR BROWSER - Dangers et Prcautions. TOR Browser Onion Web VPN comes with optimal settings of its own designed to ensure you can safely visit the vice city market darknet deep web/dark web, and/or darknet anonymously. Tor wraps the sender's message in layers of encryption rather like the layers of an onion, which is how the system got its name. Searches or messages sent via. Social media giant Facebook has officially made it possible to access their network via dark web service, Tor (The Onion Router). The FBI found Eric Marques by breaking the famed anonymity service Tor, and officials won't reveal if a vulnerability was used. That has.
Tor is open-source software for enabling anonymous communication on the Internet. It obfuscates the source and destination of a web request by. Different darkweb marketplaces offer to buy illegal drugs online like LSD, The Dark Web (D Agora was a darknet market operating in the Tor network. Results 1 vice city darknet market - 10 of 11822 Dark Web Rindexx topic links for alice in wonderland and other things. onion Deep Web links, install Tor Browser from torproject. Dark Web monitoring is just like network monitoring, but instead of monitoring your network (and known traffic), you're monitoring a list of Tor sites, IP. The dark web isn't indexed or searchable by normal search engines, and to access it, individuals must use an anonymized browser called Tor. By M Chertoff 2017 Cited vice city link by 89 The site also must require a user to input its unique Tor address. Some Dark Web sites have an additional layer of security and may also require users to input.
Dark net markets that are in languages other than English or are targeted at specific countries. However, Tor is not ideal, so for many users the question. TOR allows users to obfuscate browsing activity by scrambling a user's IP address through a secure and distributed network. The TOR project also. The dark web is where users can access unindexed web content anonymously. users need a special browser, the most common of which is Tor. The Tor darknet Browser is an open-source deep browser that's available for Windows, Mac, and Linux computers, as well as Android mobile devices. This was the. What are the different parts of the internet? Why do people use Tor to access the dark web? I've just discovered that my child is using Tor. What should I do. Onion URLs from the Tor network, then feeds these pages to their index provided that they don't contain a tor dark web file saying not to index.
Silk Road Darknet Market
They're going to want to see history of crime," says Radware's Smith. Now that it has been shown conclusively that sites of this kind are legally vulnerable, it is possible that some users would like to leave the medium entirely and go back to in-person transactions. NFTMP, illegal importation only made up one per cent of total diversions. ToRReZ Market Is now one of the biggest DarkNet Markets, and since it focuses on security and keeping their customers and vendors and userssafe.. CP-000142-MW The following information is being provided by the FBI, with no guarantees or warranties, for potential use at the sole discretion of recipients in order to protect against cyber threats. Coming from a very small village (population around 3000), that was absolutely the case back then. Closed Captioning and Described Video is available for many CBC shows offered on CBC Gem. Ultimately, the FBI linked the computer tor dark web at the Hickory Street apartment and its IP address to code on the Silk Road server that allowed the computer access, court tor dark web papers say. Once you're ready to buy your favourite pony, you'll have to pay, and credit cards are not acceptable in crypto circles (because transactions can be repudiated). Assuming prices remain the same, these savings would be retained by the sellers.
“If you fancy checking out another dark-web-based social network or forums with news and discussions too, Dread is a great alternative. A post on dark web forum NetWalker Blog shows large numbers uk darknet markets of files which appear to be taken from financial services company Staircase Financial Management.”
Silkkitie Darknet Market
Each level offers a wider variety of products and services that you can offer to our buyers. According to Bergman’s white paper, the vast majority of the World Wide Web resides below the surface, where pages and URLs are not found by search engines. Buy Bitcoins with Credit Card: Bitcoins have been around for quite some time now, but even today. Nicholas Weaver, a security researcher at Berkeley's tor dark web International Computer Science Institute, speculates that __the remaining sites may have been hosted in countries beyond western law enforcement's reach. All buyers, vendors and support will approach each other with mutual respect. Congestion can occur when a network experiences an unusual spike in activity that surpasses the volume the network was designed to handle, or in the event of certain malicious attacks such as a Distributed Denial-of-Service (DDoS) attack. They pre-empt the move by firmly taking down the platform, working off with any customer funds they eventually hold at the time.
You can follow us on Linkedin, Twitter , Facebook for daily updates.